Hook, Subject Line, and Sinker: How Phishing Attacks Reel You In
This article contains real images of communications used by phishing scammers to attempt to obtain personal information of two members of the moneyinfo team. When it comes to phishing and other security measures, you should follow the advice provided by the internet security protocols your company has issued.
What is a phishing attack?
How can this be prevented?
What is the danger for Financial Advisers?
So what should I do?
“That’s okay, I use post”
Surviving phishing season
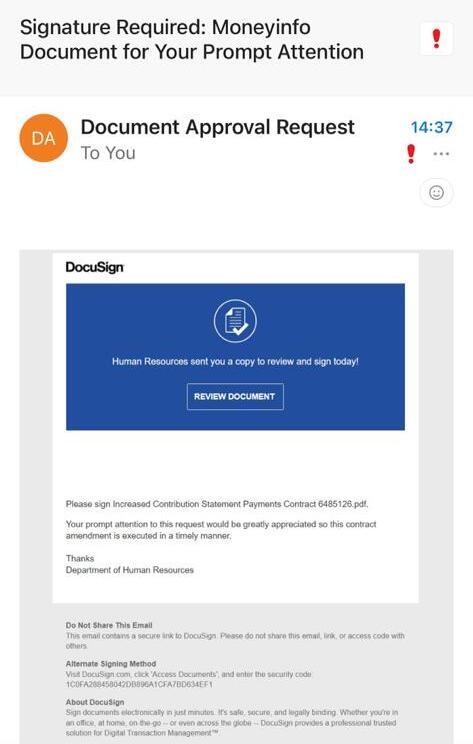
Recently, our managing director at moneyinfo, Tessa Lee, experienced a phishing attack attempt disguised as DocuSign, the third most impersonated brand by scammers.
To shed light on this prevalent issue, we have decided to share exactly what this email looked like to inform others of just how sophisticated these attacks currently are.
Here’s the email:
What is a phishing attack? | back to the top
Phishing is when scammers attempt to trick users into clicking a link that will download malware, or direct them to a potentially dangerous website in order to obtain personal information.
By this point, you should have received training on the warning signs to look out for when it comes to phishing scams, or you should at least be aware of common themes.
Typically you should look out for typos, bad formatting, or the lack of a logo, but with emails like the above, the warning signs aren’t as visible when the criminals are more sophisticated and attackers are taking further steps to appear to be sending from a trusted source.
How can this be prevented? | back to the top
There is no prevention when it comes to using email, as your inbox can basically be accessed by anyone despite junk email filters.
If an email address has historically received low open rates, high bounce rates, and a lot of spam complaints, they will receive a poor IP reputation and are more likely to be blocked by spam filters. So yes, spam filters work against email addresses which have a bad ip reputation, but this doesn’t mean attackers can’t just create new email addresses and catch you off guard. If somebody wants to email you, they will find a way to do it.
Think of your inbox as an unlocked door. You will expect only people you know to come into your house, but if there is one bad apple trying to open every door in the neighbourhood, eventually they will get into your house.
What is the danger for Financial Advisers? | back to the top
This is a big risk for clients of Advisers, especially if Advisers typically use DocuSign through email, as it may be indistinguishable from normal communications. Clients may receive emails regularly that look like this and not think twice when signing important documents straight from their inbox.
We strongly advise against using DocuSign via email. It’s definitely worth clients being able to tell the signs of a phishing attempt but shouldn’t be the only form of defence for them.
So what should I do? | back to the top
It’s simple, tell your clients not to use email to send or receive any sensitive documentation, and especially not DocuSign.
This should be regularly communicated and you should remind them whenever possible that emails shouldn’t be clicked on when asking for personal information such as passwords, signatures, or security questions.
Mobile apps should be used for this purpose instead of email, with biometric access, nobody can access your clients’ information but your client.
With using an app for all of your communications, features such as secure messaging, DocuSign e-signatures, and push notifications accompanied by your brand logo are paramount for your clients’ security and peace of mind.
“That’s okay, I use post” | back to the top
You might think you’re safe but your clients aren’t, especially if they trust post as much as most people do. When we think of physical documentation, it’s easy to believe fraud isn’t as sophisticated as the phishing email previously shown in this article, but here’s an example of a ‘physical phishing’ attempt:
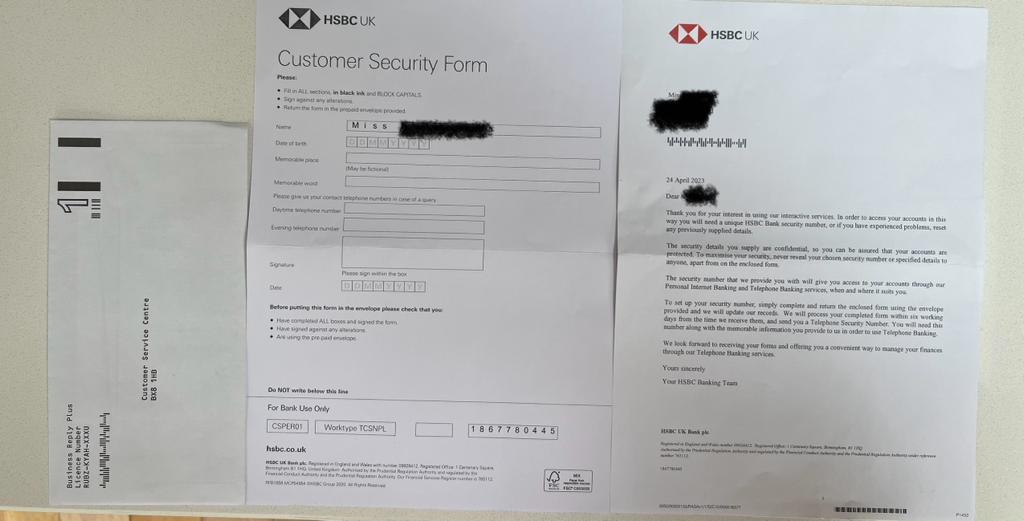
The above may look official, but it’s another attempt to take advantage of the recipient and get them to hand over sensitive, important information that can negatively impact the life of the victim when put into the wrong hands. The document even includes information about the recipient, moneyinfo’s own Business Development Director, Sim Sangha. It’s hard to know how scammers obtained his personal information, but the importance of this article is to highlight how surprisingly detailed and sophisticated these attacks can be.
If you want to survive phishing season, don't go in the water. | back to the top
We mean it, there are some nasty monsters lurking in the email inboxes of even the most vigilant, attentive eyes and the best way to avoid phishing attacks is to not give yourself or your clients the opportunity to get caught out.
The features we mentioned earlier really are the best form of defence against security vulnerabilities, here is a quick list of ways they can help:
DocuSign e-signatures : If your clients know the only place to sign anything is in the app you provide for them, they will ignore everything else with complete peace of mind.
Secure messaging : Encrypted messaging in a WhatsApp style format that they’re used to, great for seeing the whole history of the conversation which can be used as an audit trail.
Push notifications : Like we said, email is murky waters and your clients will have to swim through a lot of noise to get your communications. The post is even less instant. With push notifications delivered straight to your branded app on their mobile device, clients can immediately see when you need them, what you need, and respond within minutes, not days.
…Did we mention directing clients to log into your app is the most secure method of communication? I think we did.
If you want to get a full demonstration of these powerful Digital Relationship Management (DRM) features that help to keep your clients safe from attackers, get in touch here to book a personalised demonstration.